Additional manual configuration is required.
This page describes the Markets in Financial Instruments Directive (MiFID) II and the relevant features within Eleveo products. It is divided as follows:
What Is the 'Markets In Financial Instruments Directive - MiFID' and 'MiFID II'?
The Markets in Financial Instruments Directive (MiFID) is a European Union law that standardizes regulation for investment services across all member states of the European Economic Area. MiFID II is a legislative framework instituted by the European Union to regulate financial markets in the bloc and improve protections for investors with the aim of restoring confidence in the industry after the financial crisis exposed weaknesses in the system.
The Directive mainly impacts upon the procedures which employees must follow with regards to customer interactions, call recording, digital communications and record keeping. In the Directive customer interaction records are covered primarily in Articles 16 and 69.
Eleveo Supports Full Compliance With the MIFID II Regulation
Eleveo supports the core MiFID II requirements:
-
Capturing Relevant Interactions
-
Identifying - Tagging Relevant Interactions
-
Keeping Relevant Interactions
-
Auditing Data Flow and Data Access
-
Access Audit Logs and Media Files
-
Complaints Management
-
Complaints Training
-
Monitoring Complaints Conformity
MiFID II Compliance Features
Eleveo provides full compliance with the following relevant MIFID II objectives:
|
Control Objective |
MIFID II Requirements |
V 9.x |
|---|---|---|
|
Capturing Relevant Interactions |
1. Capturing any information provided to clients in telephone calls. > Powerful Recording Rules 2. Capturing any information provided to clients using another digital form of communication. > Chat and Email Importer 3. Capturing any information provided to clients in telephone calls outside the company. > Recording |
|
|
Identifying Relevant Interactions |
4. Identifying relevant interactions by automatic tagging. > Automatic tagging 5. Identifying relevant interactions by manual tagging. > Manual tagging |
|
|
Keeping Relevant Interactions |
6. Keeping relevant interactions and protecting them against deletion for the period of 5 or 7 years. > Delete protection |
|
|
Auditing Data Flow and Data Access, Audit Logs and Media Files |
To the competent authority shall be given the possibility to: 7. Be able to investigate data flows and data access. > Audit logs 8. Inspect Audit Logs or their exports. > User permissions and Audit log 9 On request, listen to or view the recordings. > Media export |
|
|
Complaints Management |
10. Firms shall establish a complaints management program.> Quality Management as a package supports this requirement |
|
|
Complaints Training |
11. Investment firms shall educate and train employees in procedures governing the regulation requirements. > Training |
|
|
Monitoring Complaints Conformity |
12. Investment firms shall periodically monitor the records of transactions. > Reviews |
|
In order to assist your compliance obligations we provide the following features:
-
User Permission and Audit Logs
1. Recording Rules
On-Premise Solution
Recording Rules provide an “opt-in” consent capability to ensure the call recording channel supports the additional level of detailed consent that the MiFID ll requires. Agents can contractually ask for consent during a call, and the customer’s consent can be recorded or added to the recording as meta-data—for example, to capture why something was recorded. Using the Eleveo Conversation Explorer, Compliance Analysts can search for personal information by various email and chat fields,including to/from/cc and the body of text-based conversations as well as call metadata.
Cloud Solution
Recording in the Cloud is dependent on the Cloud solution configured for your particular installation. The administrator for your integration will know more. Using the Eleveo Conversation Explorer, Compliance Analysts can search for personal information by various email and chat fields,including to/from/cc and the body of text-based conversations as well as call metadata.
Please contact an Eleveo representative for details.
2. Chat and Email Importer
Conversation Explorer Search Engine is a unique omni-channel conversations platform that is embedded in the Quality Management application in the form of the Conversation Explorer. The search engine expands the voice and screen design in Quality Management to other communication channels such as emails and chats, while also leveraging the existing user management, authentication, and authorization services.
The search engine behind the Conversation Explorer in Eleveo Quality Management with a built-in media player and support for the import of multiple source formats including Email and Chat.
3. Recording
Please contact an Eleveo representative for details.
4. and 5. Call Tagging
Tagging enables the Identification of Relevant Interactions. We provide the possibility to automatically tag conversations based on attributes or manually tag calls. The following section describes the various ways that tags can be applied.
Call segment tagging can be configured in:
-
Recording rules (automatic tagging)
-
API (Tagging by 3rd party application)
-
Cisco Finesse Gadgets (Manual tagging)
-
Using any external data (Automatic tagging with Contact Center Integration)
Recording Rules (Automatic Tagging) (on-premise and hybrid deployments only)
Automatic tagging is configurable separately for each recording rule. If the call segment matches the recording rule, the TAG will be added to the specific call segment. Both Phone number-based and External data-based recording rules can be used.
The recording rules are processed from TOP to DOWN.
Example:
-
1st recording rule: Record Extension 2180 without TAG
-
2nd recording rule: Record Extension 2178 with TAG
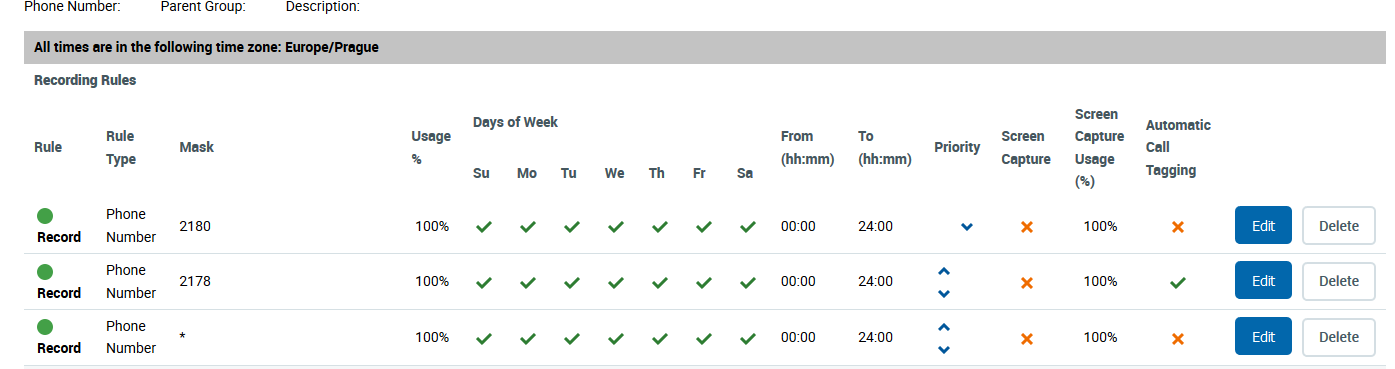
Tagging
-
When a customer calls extension 2178, the call segment will be tagged, because the 2nd rule is matched.
-
When a customer calls extension 2180, the call segment will NOT be tagged, because the first recording rule is matched.
-
Each call segment between extensions 2180 and 2178 will NOT be tagged, because the first recording rule is matched.
API (Tagging by 3rd Party Application)
Tagging via API is functional only when the call is actively recorded. Tagging does not require that there be a special recording rule with tagging enabled.
Tagging via API requires the configuration of TAGs by an Eleveo administrator.
-
TAG is attached to the active call segment only. If all call segments have to be tagged, each call segment has to be tagged separately.
-
If the call is on HOLD or RTP streams are not captured, the system responds with "no active call" information.
Cisco Finesse Gadgets (Manual Tagging) Hybrid deployments only
Cisco Finesse Gadgets uses the API functionality and displays the same limitations as seen with API tagging. This tagging does not require any special recording rule with tagging enabled.
Tagging via API using Cisco Finesse Gadgets requires the configuration of TAGs by an Eleveo administrator.
If the call is on HOLD or RTP streams are not captured, the system responds with "no active call" information.
A TAG is attached to the active call segment only. If all call segments have to be tagged, each call segment has to be tagged separately.
Configuring MLM
Call delete protection
In order to protect tagged call segments from deletion by the MLM tools it is necessary to add additional configuration to the Delete Tool. This configuration does not require that advanced search fields be configured. Call segment without the TAG will be deleted as set by the delete tool task settings.
Archive tagged calls to separate directories (on-premise and hybrid deployments only)
In order to be able to archive tagged calls to a separate directory is required to configure an advanced search field for TAGs represented by an External Data Key. The configuration of advanced search fields is in Settings > Configuration > Web UI > Search. After the advanced searches are set up the External Data Key name appears in the drop-down menu of call selection for archiving in Settings > Configuration > Maintenance > Archive. Setup the condition for TAG value for the specific archive task. Each archive task provides the possibility to save archive files into a separate destination directory into which can be mounted separate network drive.
Call Flow Examples and Call Tagging (on-premise and hybrid deployments only)
This paragraph describes basic call flows with a description of which call segments have the TAG attached after they are saved into the DB.
Basic call (no hold, no transfer)
-
REC Rules: Customer calls to extension 2178 with configured tagging in Rec Rules (TAG)
-
API: Customer calls Agent and tag is added via API (TAG_API)
-
Gadgets: Customer calls Agent and tag is added via Finesse Agent Desktop (TAG_FIN)
-
UCCE IM: Customer calls Agent and tag is added by UCCE IM (TAG_CCE)
|
|
Rec rules |
API |
Gadgets |
UCCE IM |
|---|---|---|---|---|
|
1st segment |
TAG |
TAG_API |
TAG_FIN |
TAG_CCE |
Basic call with hold (no transfer) - 1st segment
-
REC Rules: Customer calls to extension 2178 with configured tagging in Rec Rules (TAG)
-
API: Customer calls Agent and tag is added via API (TAG_API) before HOLD
-
Gadgets: Customer calls Agent and tag is added via Finesse Agent Desktop (TAG_FIN) before HOLD
-
UCCE IM: Customer calls Agent and tag is added by UCCE IM (TAG_CCE) before HOLD
|
|
Rec rules |
API |
Gadgets |
UCCE IM |
|---|---|---|---|---|
|
1st segment |
TAG |
TAG_API |
TAG_FIN |
TAG_CCE |
|
2nd segment |
TAG |
- |
- |
TAG_CCE |
Basic call with hold (no transfer) - 2nd segment
-
REC Rules: Customer calls to extension 2178 with configured tagging in Rec Rules (TAG)
-
API: Customer calls Agent and tag is added via API (TAG_API) after HOLD
-
Gadgets: Customer calls Agent and tag is added via Finesse Agent Desktop (TAG_FIN) after HOLD
-
UCCE IM: Customer calls Agent and tag is added by UCCE IM (TAG_CCE) after HOLD
|
|
Rec rules |
API |
Gadgets |
UCCE IM |
|---|---|---|---|---|
|
1st segment |
TAG |
- |
- |
- |
|
2nd segment |
TAG |
TAG_API |
TAG_FIN |
TAG_CCE |
Transferred call (blind transfer)
-
REC Rules: Customer calls to extension 2178 (2nd rec rule) with configured tagging in Rec Rules (TAG). After that the call is transferred to extension 2180 (1st rec rule) with recording rule set WITHOUT tagging
-
API: Customer calls Agent and tag is added via API (TAG_API) before TRANSFER. After that the call is transferred to extension 2180.
-
Gadgets: Customer calls Agent and tag is added via Finesse Agent Desktop (TAG_FIN) before TRANSFER. After that the call is transferred to extension 2180.
-
UCCE IM: Customer calls Agent and tag is added by UCCE IM (TAG_CCE) before TRANSFER. After that the call is transferred to extension 2180
|
|
Rec rules |
API |
Gadgets |
UCCE IM |
|---|---|---|---|---|
|
1st segment |
TAG |
TAG_API |
TAG_FIN |
TAG_CCE |
|
2nd segment |
- |
- |
- |
TAG_CCE |
Transferred call (consult transfer)
In this scenario 3 segments will be created:
-
Customer - Agent1 (2178)
-
Consultation Agent1 (2178) and Agent 2 (2180). This consultation is evaluated as a separate call
-
Customer - Agent2 (2180)
-
REC Rules: Customer calls to extension 2178 (2nd rec rule) with configured tagging in Rec Rules (TAG). After that the call is transferred to extension 2180 (1st rec rule) with recording rule set WITHOUT tagging.
-
API: Customer calls Agent and tag is added via API (TAG_API) before TRANSFER followed by consult and transfer to extension 2180.
-
Gadgets: Customer calls Agent and tag is added via Finesse Agent Desktop (TAG_FIN) before TRANSFER followed by consult and transfer to extension 2180.
-
UCCE IM: Customer calls Agent and tag is added by UCCE IM (TAG_CCE) before TRANSFER followed by consult and transfer to extension 2180.
|
|
Rec Rules |
API |
Gadgets |
UCCE IM |
|---|---|---|---|---|
|
1st segment |
TAG |
TAG_API |
TAG_FIN |
TAG_CCE |
|
2nd segment |
- |
- |
- |
- |
|
3rd segment |
- |
- |
- |
TAG_CCE |
Basic call with hold with updating TAGs
In this example will set TAG_XX=1 which is changed to TAG_XX=2 before HOLD. After the HOLD the TAG_XX is changed to TAG_XX=3.
-
REC Rules: Customer calls to extension 2178 with configured Tagging in Rec Rules (TAG)
-
API: Customer calls Agent and tag is added via API (TAG_API=1) and later changed to (TAG_API=2) before HOLD. After HOLD the (TAG_API=3) is added.
-
Gadgets: Customer calls Agent and tag is added via Finesse Agent Desktop (TAG_FIN=1) and later changed to (TAG_FIN=2) before HOLD. After HOLD (TAG_FIN=3) is added.
-
UCCE IM: Customer calls Agent and tag is added by UCCE IM (TAG_API=1) and later changed to (TAG_API=2) before HOLD. After HOLD the tag is changed to (TAG_API=3).
|
|
Rec rules |
API |
Gadgets |
UCCE IM |
|---|---|---|---|---|
|
1st segment |
TAG |
TAG_API=2 |
TAG_FIN=2 |
TAG_CCE=2 |
|
2nd segment |
TAG |
TAG_API=3 |
TAG_FIN=3 |
TAG_CCE=3 |
6. Protection Against Deletion
Please contact an Eleveo representative for details.
7. and 8. User Permissions and Audit Logs
Audit Log in User Management
For User Management, please refer to the dedicated guides.
Audit Log in Quality Management
Using the Audit Log
The Audit Log tracks all user activities within the Eleveo applications (Quality Management, as well as User Management) for enhanced security and compliance purposes. By default, viewing and using the Audit Log is only available to users with the CC Manager or Compliance Analyst roles.
-
From the left menu, select Administration > Audit Log. The Audit Log screen will display recent events.
-
Click the Reset Filters icon beside a filtering option in order to clear each of the filters individually or click on the Remove Filters icon to clear all filters.
-
Or click on the Remove Filters icon to clear all filters and revert to the default setting.
-
You may filter results by Time Period, Activity, User or Result. Click Apply to apply the selected filters. By default, events from the past 10 days are displayed.
-
The search will refresh every time the filters are changed. You can also click on the refresh icon to force refresh the results.
-
Hover over the info icon to view details of the user who performed an audited action.
-
Hover over the info icon to view the full description of the audited action (useful for longer or more detailed descriptions).
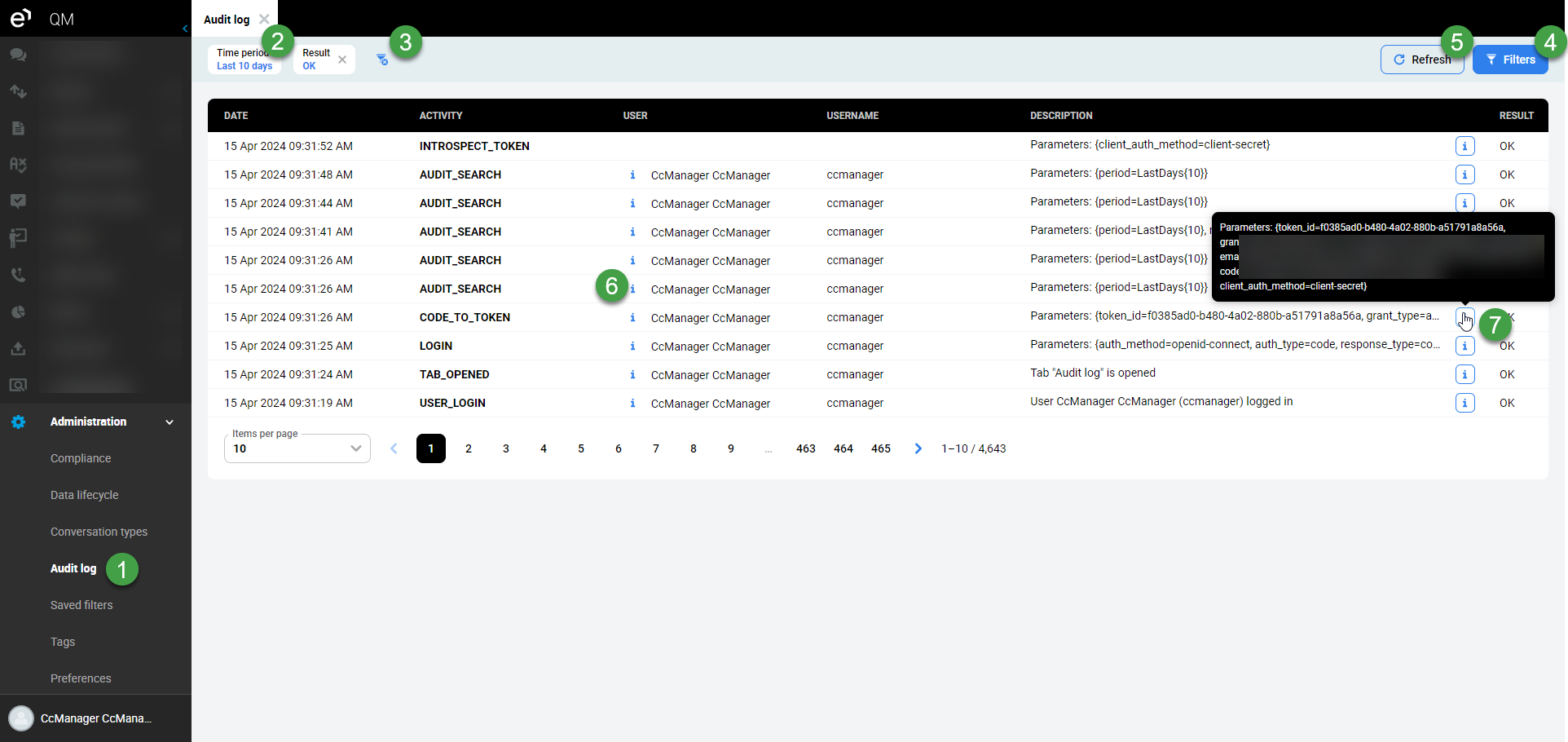
The Audit Log messages are not localized, however, the name of some items (such as the name of tabs, or other items displayed in the Web UI) are displayed in the log in the language of the audited user.
Information Displayed
The Audit Log displays the following:
-
Date: The timestamp indicates the date and time when the auditable activity occurred. The time displayed in the log corresponds to the timezone of the current user. Not necessarily the server timezone.
-
Activity: Indicates the activity that triggered the creation of the log entry. Actions displayed in this list range from; when a user logs into the application, to the creation of an evaluation, to the deletion of a call. A more complete list of activities is provided in the section below.
-
User: Displays the full name of the user who triggered the auditable action.*
-
Username: Displays the username of the user who triggered the auditable action. (The username is the same as that used on the login screen.)*
-
Description: Provides a more fine-grained detail of the activity which was logged. Usually, the details include the id of the user who performed the action, but the actual details depend on the type of activity. The description field only displays what is provided by the backend in the json file, in some cases only a user ID is displayed. If it is necessary to determine which user matches a particular id, then it is necessary to access the database directly. For example, to determine a user related to a conversation search go to the Encourage database, and examine the Table of Users.
-
Result: Status message of the Requests and Responses (see below for a detailed explanation). Each completed action is listed in the log with an indication of success (OK), failure (FAIL) or lack of permission (UNAUTHORIZED).
*Events related to users/groups import from external sources (using user importers) do no contain the User and Username information.
QM Events
The QM activities that trigger the creation of the log entry can be divided into two groups: synchronous and asynchronous.
Asynchronous Events
All actions triggered from within the Conversation Explorer and Administrative screens in Quality Management (Compliance, Audit, Data Lifecycle, UI configuration, Tags) trigger the creation of multiple records in the Audit Log list. Each received request is listed in the log without a status message. Each completed action is listed in the log with an indication of success (OK), failure (FAIL) or lack of permission (UNAUTHORIZED).
For instance, pressing the Search button on Conversation Explorer leads to the creation of two log entries, one for each action:
-
request search (begins),
-
request search (ends).
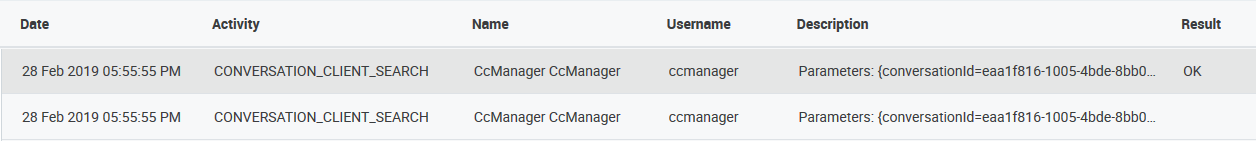
In the example provided here, the bottom row indicates that a user performed a search of conversations (no result is displayed as this is only the start of the request). The upper row indicates the successful completion of the request. Success here is indicated by the "OK" status in the Result column.
Administrators can compare the timestamp of the request received and the request completion. Long delays between the two may be indicative of connectivity related issues.
9. Media Export
To learn more about the export possibilities, please see the Export section of the Quality management guide.
10. Quality Management
Eleveo provides a complete set of integrated solutions to effectively manage your contact center or unified communications environment. For more detailed information, please consult the Quality Management - User Guide
11. Training
Eleveo enables enhanced agent training. The following section describes how eLearning is used to quickly improve knowledge transfers across contact centers.
eLearning involves either training new hires who have little or no knowledge of the subject, or training agents with low evaluation scores. Either way, good trainers know that trainees must be tested to ensure that they understand everything.
Good training includes:
-
Training instructions.
-
A reference interaction that the trainee can listen to.
-
A presentation with interactive pictures and sound.
-
A quiz to help the trainer see how well the trainee has digested all the information.
Training is usually provided in the following cases:
-
Taking new agents on board
-
Training/Coaching Packs for supervisors
-
Coaching agent performance
Taking New Agents on Board
A contact center's largest expense is employee salaries. When a company hires an agent, it faces considerable costs to train the agent, and it can take months before the company will see a return on investment. eLearning both distributes content and tests new agents, allowing them to digest important information and review it as necessary. This solution reduces time and effort across training teams by allowing them to focus on the agents that need additional help or quickly weeding out agents that may not be the right fit for the company. New agents become used to the applications and can self-study with minimal impact on their calling time. Most importantly agents are able to review areas that are difficult or challenging to be sure they know what they need to know.
eLearning and Coaching Packs for Supervisors
Supervisors are responsible for managing teams of agents and their overall performance. All supervisors are not created equal. Targeted and quick coaching helps them support agents in their daily activities. Managers can also send coaching and eLearning content directly to their supervisory team with best practices for:
-
Coaching
-
Motivation
-
Goal setting
-
Performance management
-
Disciplinary procedures
-
New processes, programs or product updates
By fully informing supervisors and team leaders of best practices, companies can make sure that these practices are implemented and calibrated across all processes. To this end all eLearning packs include a quiz to ensure uptake and measurable understanding of the content. This lets the contact center know that everyone is up to date and are all working in the same direction.
Coaching Agent Performance
It's an extremely tough job to ensure that all agents meet company KPIs. When one agent improves it’s likely another drops, and the effort to keep all agents on a path of continuous improvement is difficult at best. eLearning allows supervisors to provide training and coaching to all agents under their management with a few clicks. This guarantees that every agent receives the same information. While freeing supervisors to review and measure test results.
Reports relevant to Training/eLearning
The most relevant reports for E-Learning are Review Volume report and League Table report.
12. Reviews
We support regular review of conversations via built-in review functionality. For more detailed information, please see the relevant documentation.
The Reviews pages guide you through the review process in contact centers, such as creating and using standardized reviews or generating standardized review data using Quality Management.
The following pages describe the steps in the review process.
-
Creating New Reviews -
Using the Reviews Screen -
Review Notifications -
Adding Specific Conversations for Review -
Add Random Conversations for Review -
Conversation Review - Grading Form -
Completing a Review -
Deleting Reviews -
Reopening a Review -
Using the Review Report -
Using the Review Form -
Replacing Conversation in the Review -
Review Scheduler
V 9.x does not support the import of reviews that use sub-criteria.
