Viewing Events
Overview
The Events tables allow a user with proper privileges (the manage-events role, assigned to eleveo.admin by default) to view the login and admin events log from within UI.
To view the events, click Events within the navigation tree on the left. The Events screen will display.
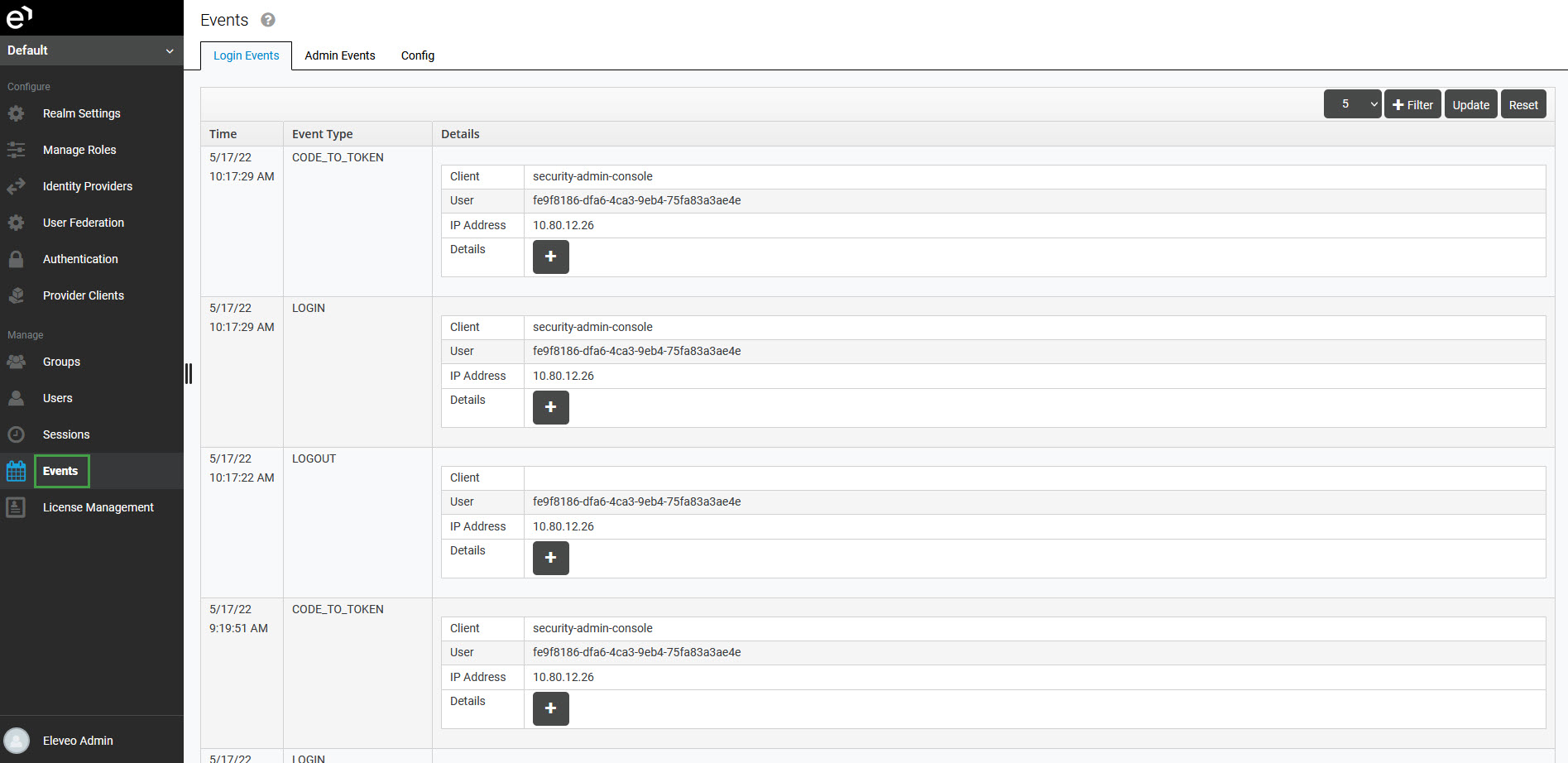
Use the drop-down menu in the top right corner to select how many events should be displayed on the page.
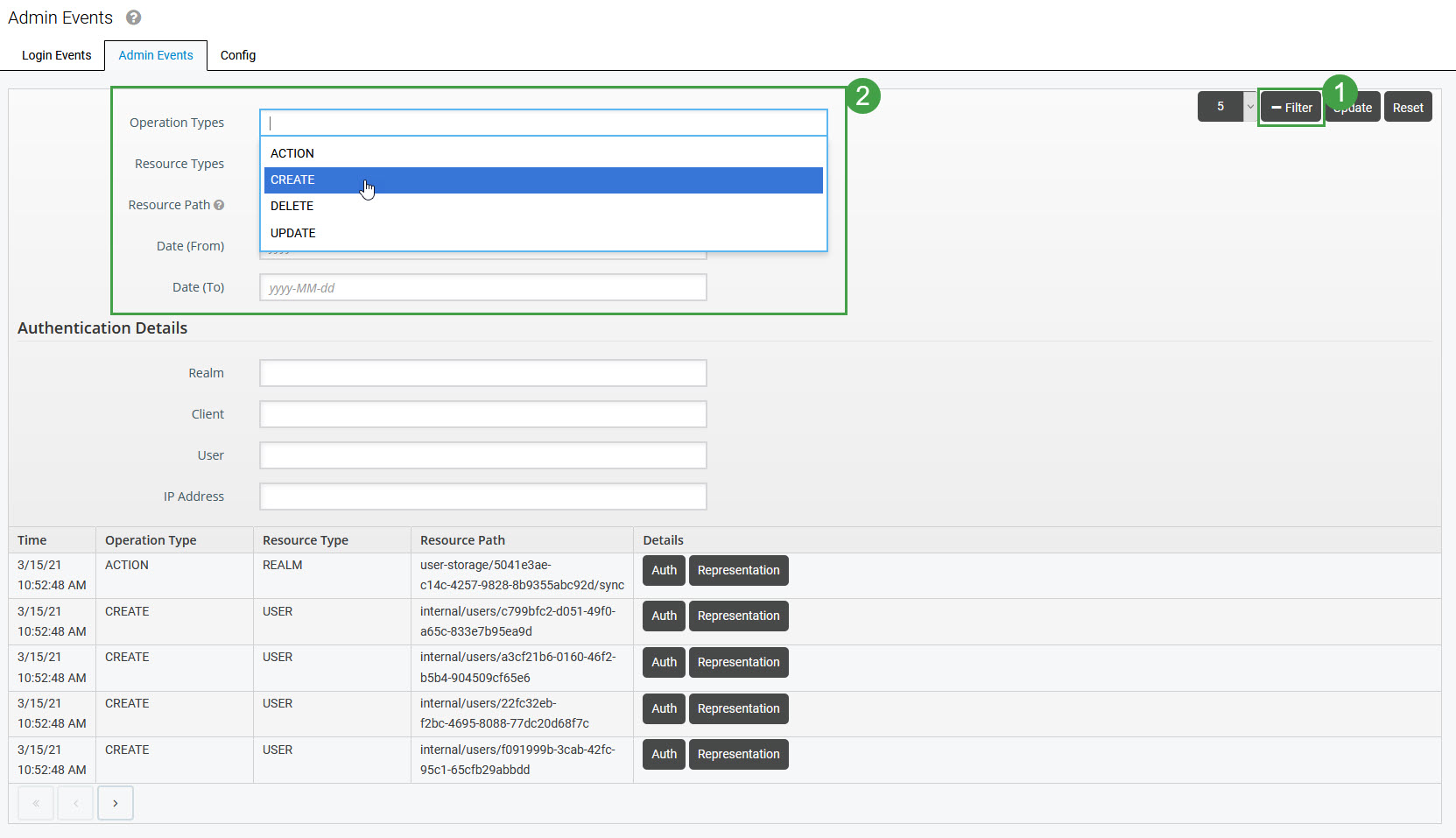
Click Filter in the top right corner to expand the filtering options.
Login Events
All access-related activities performed by users (for example login, logout, requesting a token, etc.) are recorded for auditing purposes in the table on the Login Events tab.
Login Events can be viewed by:
any user with the
manage-eventsrole (eleveo.admin by default) – in the User Management admin console (Events > Login Events tab)any user with the
VIEW_AUDITpermission for QM (default_ccmanager by default) – in the Quality Management console (Administration > Audit Log)
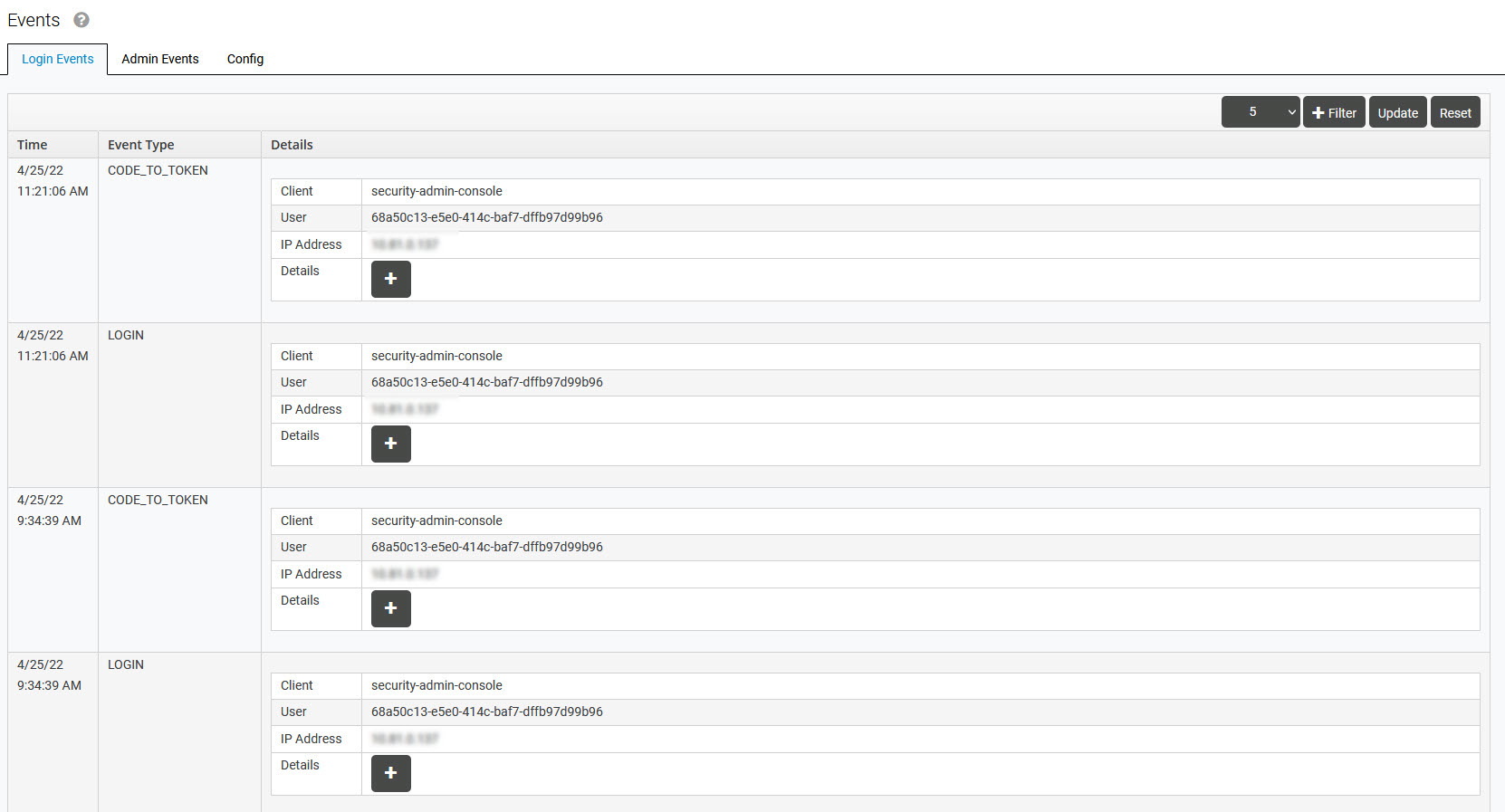
The table contains all logged events and their details:
Time – exact time of the event
Event Type – type of the event (for example LOGIN, LOGOUT etc.)
Details:
Client – ID of the client to which the user is connecting
User – IP of the user
IP address – IP address from which the user is connecting
Details – Further details about the token
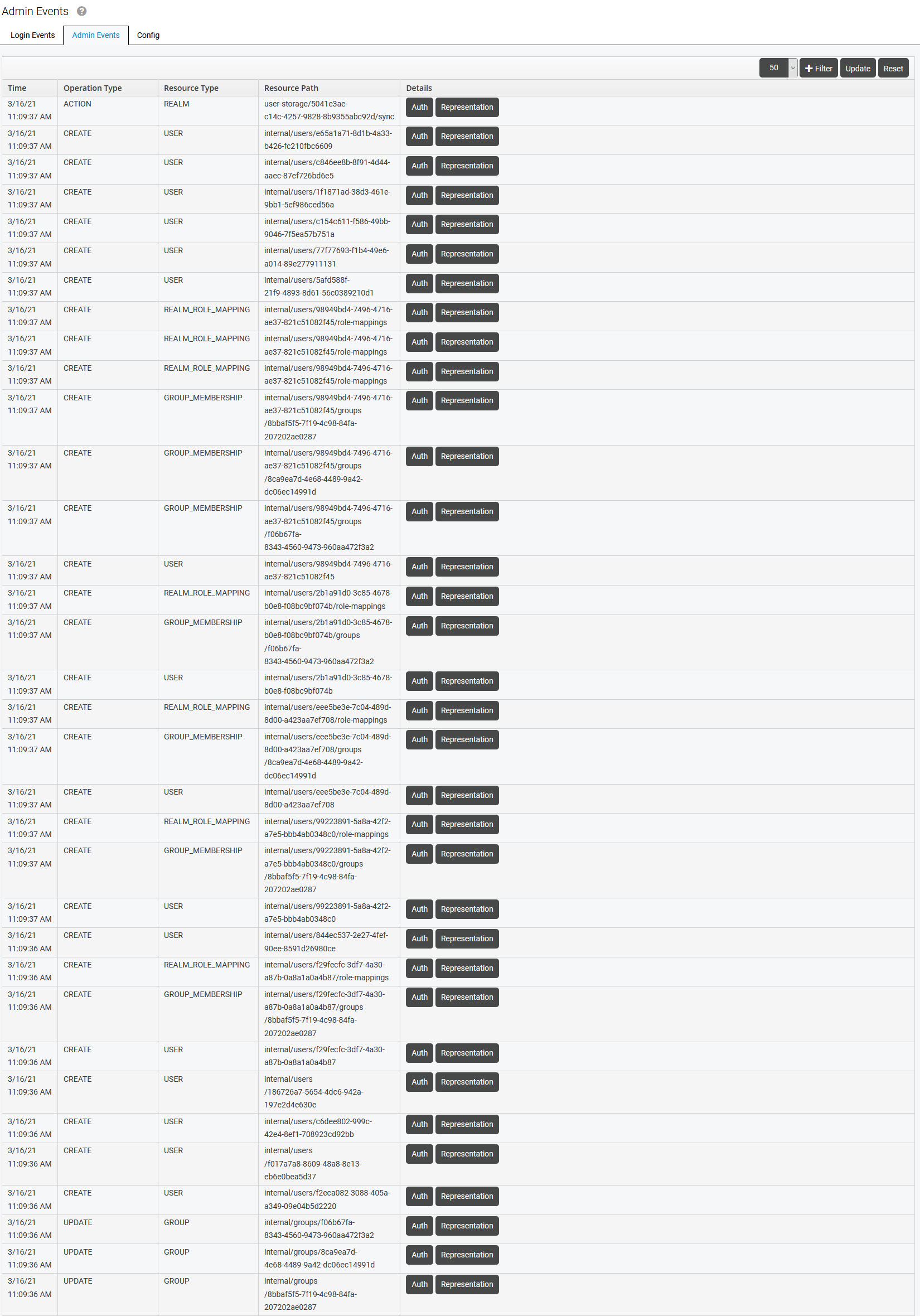
Admin Events
All actions performed by any user with enough privileges to complete these actions within the admin console are recorded for auditing purposes in the table on the Admin Events tab.
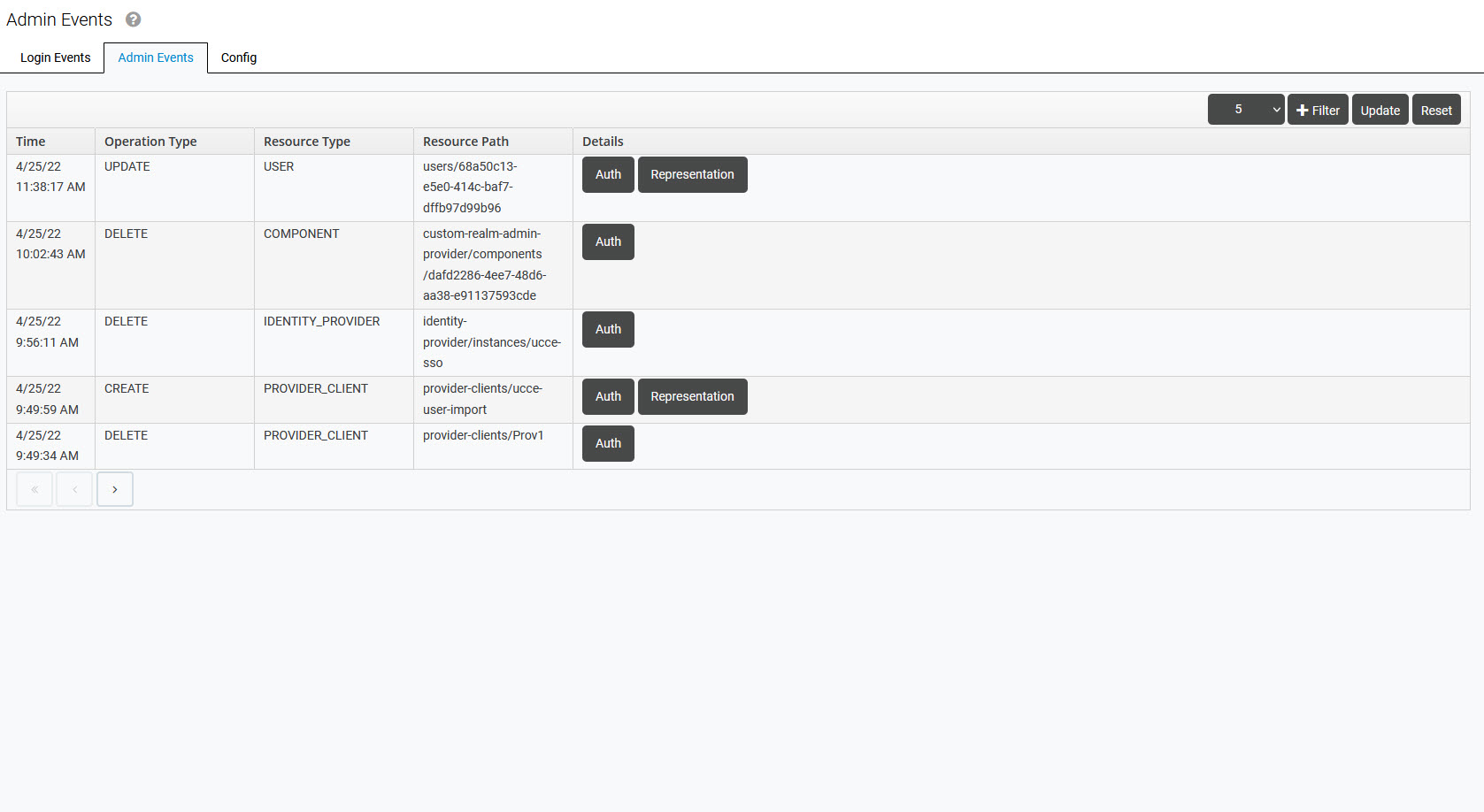
The table contains all logged events and their details:
Time – exact time of the event
Operation Type – type of the event (for example CREATE, UPDATE, DELETE, etc.)
Resource Type – resource which is affected by the event (for example USER, GROUP, etc.)
Resource Path – path to the affected resource
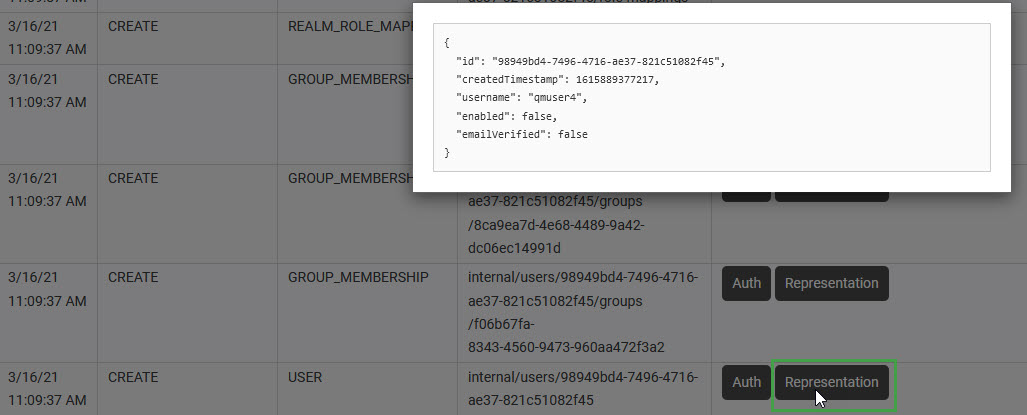
Details:
Auth – authentication details of the user who has triggered the event
Representation – JSON content representing the event
Types of Events
The following Admin Events can be logged:
Scope/area | Operation Type | Resource Type* | Description |
|---|---|---|---|
Users | CREATE | USER | Creating a user |
UPDATE | Updating a user's details | ||
DELETE | Deleting a user | ||
DELETE | IMPORTED_USERS | Deleting an imported user | |
Groups | CREATE | GROUP | Creating a group |
UPDATE | Updating a group's details | ||
DELETE | Deleting a group | ||
CREATE | GROUP_MEMBERSHIP | Creating an assignment of a user to a group (group membership) | |
UPDATE | Updating a group membership | ||
DELETE | Deleting a group membership | ||
CREATE | CLIENT_ROLE | Creating a client role | |
UPDATE | Updating a client role | ||
DELETE | Deleting a client role | ||
CREATE | CLIENT_ROLE_MAPPING | Creating a mapping between a user and a client role | |
UPDATE | Updating a mapping between a user and a client role | ||
DELETE | Deleting a mapping between a user and a client role | ||
CREATE | REALM_ROLE | Creating a realm role | |
UPDATE | Updating a realm role | ||
DELETE | Deleting a realm role | ||
CREATE | REALM_ROLE_MAPPING | Creating a mapping between a user and a realm role | |
UPDATE | Updating a mapping between a user and a realm role | ||
DELETE | Deleting a mapping between a user and a realm role | ||
Custom roles | CREATE | CUSTOM_ROLE | Creating a custom role |
UPDATE | Updating a custom role | ||
DELETE | Deleting a custom role | ||
CREATE | CUSTOM_ROLE_MAPPING | Creating a mapping between a user and a custom role | |
UPDATE | Updating a mapping between a user and a custom role | ||
DELETE | Deleting a mapping between a user and a custom role | ||
Provider clients | CREATE | PROVIDER_CLIENT | Creating a provider client |
DELETE | Deleting a provider client | ||
Password management | ACTION | USERS | Changing a local users' password |
Realm settings | UPDATE | REALM_SETTINGS | Updating a realm's setting |
Supervisors | CREATE | SUPERVISOR_MEMBERSHIP | Assigning a group to a user so that the user can review this group (a supervisor membership) |
UPDATE | Updating a supervisor membership | ||
DELETE | Deleting a supervisor membership | ||
Users extended JPA | UPDATE | USER_EXTENSION | Update of the user data extension (mainGroup, timezone and syncEnabled values) |
Data Importer (pusher) | ACTION | PUSHER_SYNC | Synchronization with data importer (on-premise data provider has called API and data it sent are being processed and imported to User Management) |
License-api-provider | CREATE | LICENSE | Creating a license |
*The following Resource Types are custom and were added on top of existing ones: CUSTOM_ROLE, CUSTOM_ROLE_MAPPING, PUSHER_SYNC, PROVIDER_CLINT, REALM_SETTINGS, SUPERVISOR_MEMBERSHIP, USER_EXTENSION, LICENSE
Synchronization Events
Note that user federations' synchronization is logged granularly. The following events can be logged as a part of it:
CREATE | UPDATE
USER
GROUP
CLIENT_ROLE
REALM_ROLE
REALM_ROLE_MAPPING
CLIENT_ROLE_MAPPING
GROUP_MEMBERSHIP
SUPERVISOR_MEMBERSHIP
Configuration
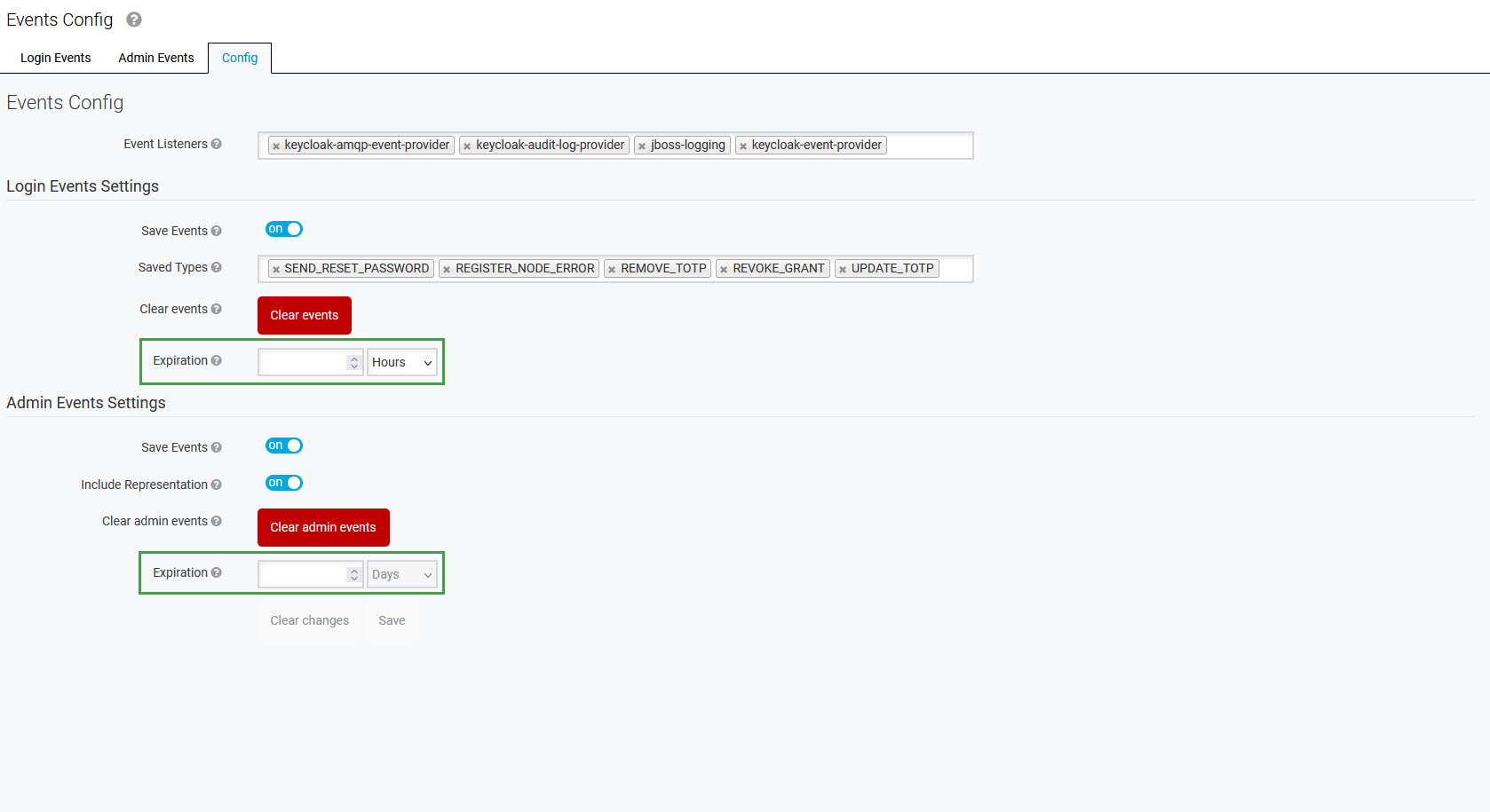
The Events settings are configured automatically during the realm registration process so that there is no need to change them or configure them manually. To ensure that Events are set as required, ensure that they are configured in the following way:
Event Listeners selected:
keycloak-audit-log-provider
keycloak-amqp-event-provider
jboss-logging
keycloak-event-provider
in the Login Events Settings section:
Save Events: ON
in the Admin Events Settings section:
Save Events: ON
Include Representation: ON
The above configuration ensures that activities triggered from within User Management (Login Events) will be included in the Audit Log in Quality Management. Read more about using Audit Log.
Events Cleanup
It can be useful to configure an expiration period for Login and Admin Events. Expired events will be automatically deleted from the database to avoid consuming too much space. By default, expiration is not set (events are not deleted).
To configure the expiration period, go to the Config tab and set the Expiration values for Login Events and Admin Events (separately). Then click Save.