CCPA Compliance
This page describes some of the compliance requirements for the California Consumer Privacy Act (CCPA) and the respective features within the solution that support compliance with the requirements of the Act. This information is provided as is and may not be complete or may not accurately reflect the requirements of the CCPA as it applies to your business case.
The information provided here does not, and is not intended to, constitute legal advice; instead, all information, content, and materials available here are for general informational purposes only. Content provided here may not be the most up-to-date information available and is provided for your convenience only.
Compliance Overview
The California Consumer Privacy Act (CCPA) is a bill intended to enhance privacy rights and consumer protection for residents of California, United States. The CCPA is of great significance to all sectors, not least due to the financial penalties and costs associated with compliance.
Compliance with the CCPA is mandatory for entities which:
Have annual gross revenues in excess of $25 million
Buys or sells the personal information of 50,000 or more consumers or households or
Earns more than half of its annual revenue from selling consumers' personal information
The Act enables California residents to:
Know what personal data is being collected about them
Know whether their personal data is sold or disclosed and to whom
Say no to the sale of personal data
Access their personal data
Request a business to delete any personal information about a consumer collected from that consumer
Not be discriminated against for exercising their privacy rights
Eleveo supports compliance with some of your obligations under the CCPA.
Eleveo Supports Compliance
Eleveo is an integral part of your company’s drive to achieve compliance. While Eleveo is not on the front lines of your strategy as it pertains to the collection and passing of personal data between a data subject and your company, Eleveo does use personal data in data processing, especially during Quality Management and Customer Experience operations. As such, Eleveo strives to provide the necessary features to ensure your compliance related initiatives.
Eleveo supports compliance with the CCPA regulation:
Consent / Opt-out
Right to Access
Right to Portability
Right to Erasure
Right to be Stop Processing
Right to stop third-party transfer
Data Deletion
CCPA Compliance Features
Eleveo offers support for full compliance with the following relevant CCPA objectives:
Control Objective | CCPA Requirements | V 9.x | How does Eleveo support compliance? |
|---|---|---|---|
Consent | 1. The individual has given clear consent for the processing of their personal data for a specific purpose and has the option to opt-out. |
| Records of Consent are Searchable. |
Right to Access | 2. Subject can obtain confirmation as to whether or not personal data concerning them is being processed, sold or transferred in the last 12 months. |
| Dependent on internal company policies, Eleveo provides the option to Export content in a readable format. |
Right to Portability | 3. The system can provide a copy of the personal data in a user-friendly electronic format. |
| Export content in a readable format. |
Right to Erasure | 4. Also known as Data Erasure is the right to be forgotten. This requires that the data controller erase personal data of a Subject upon request, and also cease further dissemination of the data. |
| The Eleveo platform has the ability to delete interactions as well as the ability to anonymize selected personal data for individual interactions based on the needs/views of the organization. Eleveo does not provide support for a process which prevents the further dissemination of the data! |
Right to be Stop Processing. | 5. Right to opt-out of selling personal data. |
| Dedicated link on company website. Implementation specific - refer to Consent. |
Right to stop third-party transfer. | 6. Right to opt-out of selling personal data to third parties. |
| Dependent on internal company policies, Eleveo provides the option to record Consent and Anonymize Data based on predefined Compliance Tags. |
Data Protection Officers | Not specifically required.
|
| Data Anonymization is a simple process for users with the Compliance Analyst Composite Role. The Audit Log provides access to records of data access attempts, and changes to data. A dedicated Compliance Tab in the UI supports the work of Data Protection Officers. Specific Compliance Tagging supports the work of Data Protection Officers. |
Security of Sensitive Data | Not specifically required.
|
| Privacy by Design is built into the System. |
Consent
On-Premise Solution
Recording Rules provide an “opt-in” consent capability to ensure the call recording channel supports the additional level of detailed consent that the CCPA requires. Agents can contractually ask for consent during a call, and the customer’s consent can be recorded or added to the recording as meta-data—for example, to capture why something was recorded. Using the Eleveo Conversation Explorer, Compliance Analysts can search for personal information by various email and chat fields,including to/from/cc and the body of text-based conversations as well as call metadata.
Cloud Solution
Recording in the Cloud is dependent on the Cloud solution configured for your particular installation. The administrator for your integration will know more. Using the Eleveo Conversation Explorer, Compliance Analysts can search for personal information by various email and chat fields,including to/from/cc and the body of text-based conversations as well as call metadata.
Please contact an Eleveo representative for details.
Export
You can export data of any selected conversation into a JSON file – an open-standard file format that uses human-readable text. You may select and export one conversation at a time. The export file is saved to the user's computer and it does not include media files.
To export a conversation Select the conversation and click Export
The following popup will appear. Click OK to save to your local device.
Compliance
When exporting conversation data, ensure that any Personally identifiable information (PII) or any other sensitive information from a customer is not included in the exported file sent to another customer or compliance party.
Data Anonymization
CCPA extends the existing, traditional definition of personal data to include online data such as:
online identifiers
cookie IDs
IP addresses
devices
other
Eleveo provides the possibility to anonymize various data fields including: phone numbers, emails, chats, text based conversations, and metadata (see Compliance). Content which is anonymized displays [anonphonenumber] or [anondigitaladdress]or in the case of IP addresses 0.0.0.0. All data selected for anonymization or pseudonymization is overwritten in the storage media and is irretrievable. For more details see the section Anonymize as described in the Conversation Explorer documentation.
Compliance Analyst Role
Eleveo products support the creation of a specialized user with elevated permissions. the Compliance Analyst is granted similar permissions as CCManager so as to be able to perform and manage compliance related activities. Only those with the appropriate permissions are able to access and select items for anonymization. By default assigned to the CC Manager and Compliance Analyst role as part of the DEFAULT_CC_MANAGER and DEFAULT_COMPLIANCE_ANALYST Default Composite Application Roles. The Compliance Analyst can View and Anonymize conversations from the Conversation Explorer, View and Edit the Compliance Tab and View and Search in the Audit Tab.
Selection of what data will be anonymized/pseudonymized can be performed from a dedicated Compliance page. Follow the steps as described on the Compliance page.
Compliance Tab in UI
Selecting PII Data for Anonymization
For compliance purposes, it is necessary to anonymize selected Personally Identifiable Information (PII). QM allows an organization to determine which PII can be anonymized based on their needs and the actual data collected by the particular installation. To be able to access and select items for anonymization you need to have a special role named INTERACTION_ANONYMIZE. By default, the role is assigned to the CC Manager and Compliance Analyst as part of the DEFAULT_CC_MANAGER and DEFAULT_COMPLIANCE_ANALYST default application roles. Refer to the section Default Composite Application Roles on the page Quality Management Roles.
To open the Compliance page, click on Administration > Compliance. Here you can select the items to be anonymized from the following sections:
Basic Data – Participants' details, such as phone number or email address and text conversations. (Saved changes in this section will be recorded as FIELD_CONFIG_UPDATE in the Audit Log)
Participant phone number – Checked by default.
Participant email or IP address – Checked by default.
Subject and body (email subject, email body, chat room name, and messages, etc.) – Unchecked by default.
Media files – Unchecked by default. Call and screen recordings. Files protected by MiFID will not be included in anonymization. (Learn more on the MiFID Compliance page)
Custom Data – Unchecked by default. All metadata configured as filters in the Conversation Explorer. (Marked as METADATA_KEY_UPDATE in Audit Log)
Other Data – Unchecked by default. All other metadata. (Marked as METADATA_KEY_UPDATE in Audit Log)
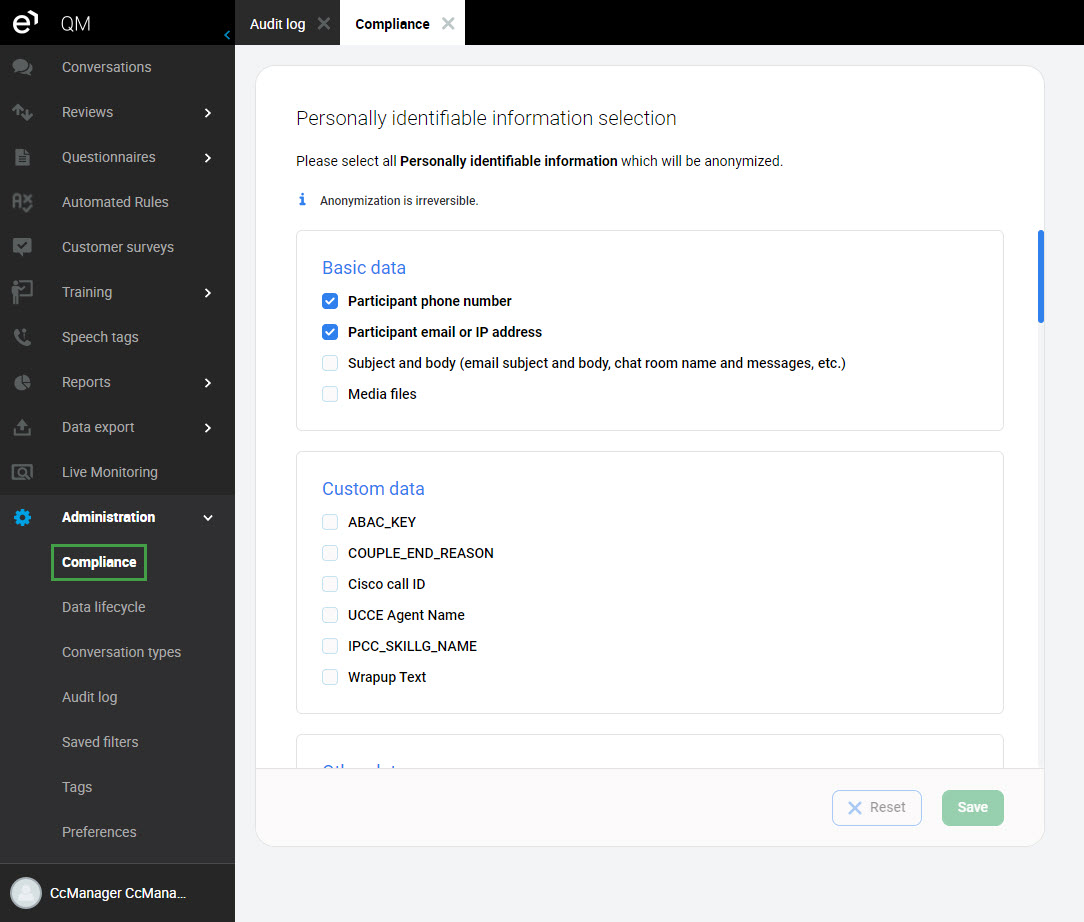
Click Save to apply your changes. Clicking Reset will revert to your last saved selection.
Data After Anonymization
Anonymized data is replaced by a placeholder text on the Conversation Explorer:
If the phone number is anonymized, then
[anonphonenumber]is displayed in its placeIf the email is anonymized, then
[anondigitaladdress]is displayed in its placeIf the chats are anonymized, then
[anondigitaladdress]is displayed in its placeIf the text conversations are anonymized, then
[anonconversationcontent] isdisplayed in its placeIf the metadata are anonymized, then
[anonymized]is displayed in its place
Make sure you do not mark for anonymization the metadata keys you configured as correlation keys used for merging conversations.
[anondigitaladdress] or [anonphonenumber] or [anonymized] or [anonconversationcontent] will be displayed by the system in place of the original PII data. The information saved to the server will be overwritten.
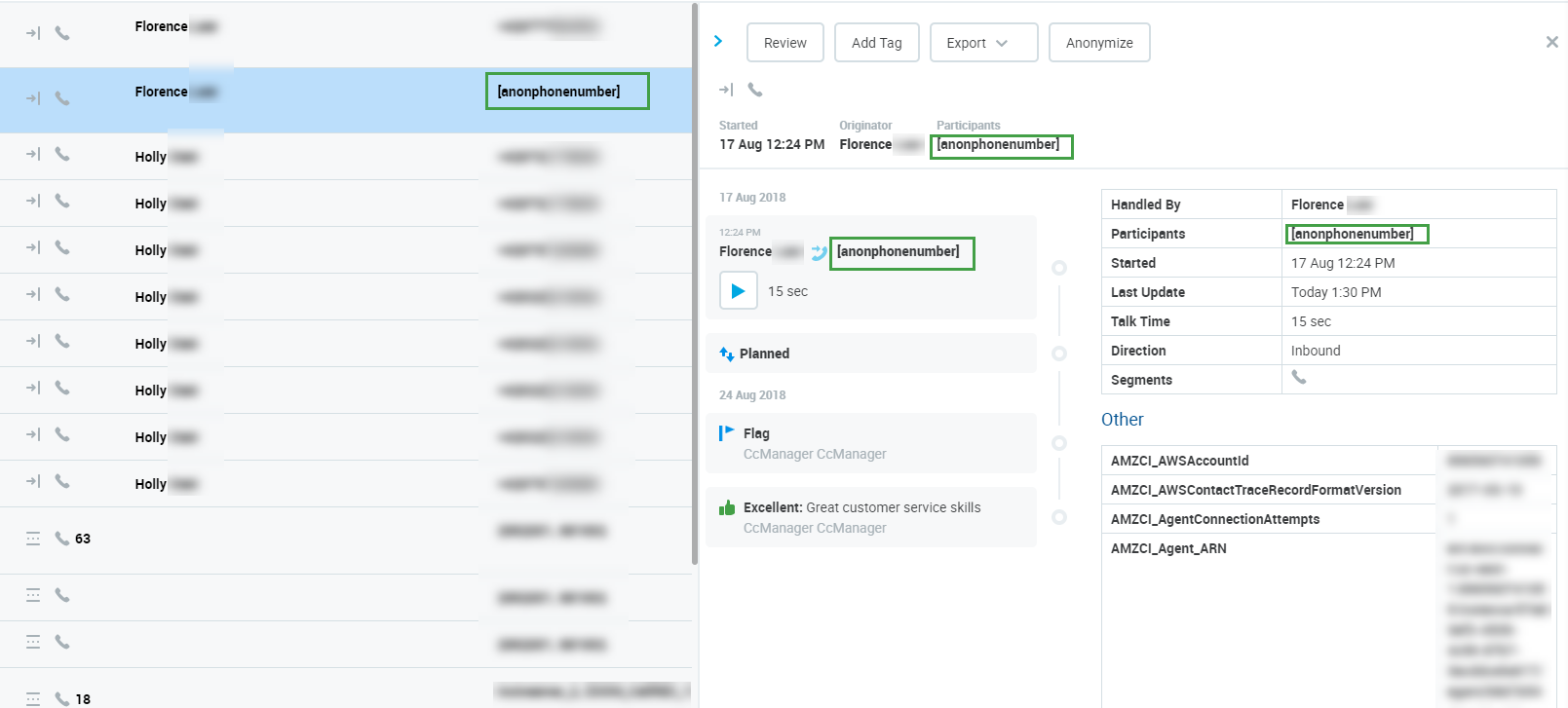
Anonymized conversations (media or text) are marked as non-reviewable in the following cases:
Call conversation with anonymized "Media files"
Chat or email conversation with anonymized "Subject and body"
Call + email or Call + chat with anonymized "Media files" and "Subject and body"
A conversation is still reviewable if at least one of its segments is not anonymized.
If the conversation's media is anonymized, then:
The conversation is marked as "Planned for deletion of media files" and a request is sent to Interaction service (media deletion). The media is still accessible and playable until the anonymized conversation media is deleted by the Delete tool. Conversation listing and detail:
icon/text with the status "Planned for deletion of media files" is displayed
If this conversation is reimported, the "Planned for deletion of media files" marking is kept
Once the conversation media is deleted by the Delete tool, the conversation is marked with "Deleted" status. The media can no longer be accessed or played. Conversation listing and detail:
an icon with the status "Deleted" is displayed
the icon representing Screen Recording in Conversation type will be deleted (the call icon is kept)
It is not possible to select which data will be anonymized from within the Conversation Explorer. Only data fields marked for anonymization as described on this page will be anonymized.
Read more about how to anonymize a conversation on the Conversation Explorer page.
Compliance Tagging
In order to mark relevant personal data for retention or anonymization, Eleveo provides specialized tagging functionality. Compliance Analyst are able to tag relevant data for retention or anonymization from within the Conversation Explorer. Enhanced functionality is provided to those with the permissions provided to the DEFAULT_COMPLIANCE_ANALYST Default Composite Application Roles. This is useful when, for example, a Compliance Analyst might want to tag some conversations for preservation by the category of lawful processing reason such as gave consent, contractual necessity, or as the content is required due to legal obligations.
Adding a Compliance Tag
To add a tag from the Conversation Explorer:
Click Add Tag.
Select the tag you wish to apply to a conversation from the dropdown list.

Click Save. The icon will change to indicate it is processing the request.

The tag field will minimize once complete.
Available tags
Compliance tags are available by default for Compliance Analysts to use.
GDPR 6(1)(a) Consent
GDPR 6(1)(b) Contractual necessity
GDPR 6(1)(c) Compliance with legal obligation
GDPR 6(1)(d) Vital interests
GDPR 6(1)(e) Public interest
GDPR 6(1)(f) Legitimate interests
If a conversation is tagged with one of the above mentioned tags, it is protected against deletion or anonymization.
For more information related to tags go to Searching by tags.
Compliance Analysts
In order to find relevant data Compliance Analysts can take advantage of the advanced search functionality provided by Eleveo products. Once the relevant data is found the Compliance Analyst can tag the conversation. See CCPA Compliance#tagging
Searching
Security
Eleveo products support compliance with a variety of security related standards. Built upon industry leading technology and best practice Eleveo products ensure the security of personal data stored in the platform. By default the programs support a security focused mindset through the following mechanisms.
Eleveo User Management Interface
User Management supports strong password enforcement policies for locally created users, as well as blocking users after multiple unsuccessful login attempts.
Default Passwords
In the new installation, only the following default users are present:
eleveo.admin – user who is assigned default administrative rights in User Management
eleveotrain – user who is used for Eleveo trainings purposes
The default users are strongly recommended to change their default passwords. A default password can be changed by a user in User Profile as described on the page Configuring User Profile and Password.
Temporary User Passwords
If the password for any user is set by eleveo.admin to be temporary, a password change is enforced when the user logs in for the first time. Setting a password to be temporary is described here: Changing Passwords for Users.
Additionally, users can change their own password using the instruction provided here: Configuring User Profile and Password.
Complex Passwords Required
By design the system requires that enhanced complex passwords be used.
Passwords must be elaborate in nature.
Eleveo default settings require that new passwords must meet the following Complexity Requirements:
at least 8 characters
with at least one character a number (0-9)
at least one character a lowercase letter (a-z)
at least one character an upper case letter (A-Z)
These settings are configurable on the Managing Password Policies page.
Regular Password Change
All locally created users are requested to change their passwords after one year.
These settings are configurable on the Managing Password Policies page.
Unsuccessful Logins Before Lockout
After 30 unsuccessful login attempts, the status of a user will change to locked. For details refer to the section Unlocking a Locked User.
Data Encryption
By design Eleveo supports the secure transmission of data between our solution and other component parts of the clients ecosystem (including user browsers, UCCE, UCCX, and Finesse Gadgets). Industry standards require the authenticated and encrypted transmission of data across networks – which includes between clients and servers in distributed systems like Quality Management . One of the functions of the Key Manager is to manage this secure transmission, including automatic transparent renewal of authentication certificates when they expire.
Key Manager
During the install process (of Call Recording) the administrator will be prompted to either: a) create a self-signed certificate and keys for the Key Manager or b) use a commercial encryption certificate.
Using a self-signed certificate (as opposed to a commercial encryption certificate offered by companies such as Thawte and Verisign) enables you to encrypt client-server communications and audio/video calls immediately after setup but can lead to issues with browsers and servers rejecting the certificate due to their weaker security status. It is, however, suitable for testing purposes.
Secure Communication
Working in conjunction with the Cisco Unified Communications Manager (CUCM) Eleveo products offers the capability of recording encrypted calls. This allows customers to maintain call security and compliance.
Audio Files Are Encrypted
Once Key Manager activates, audio encryption is enabled automatically.
Video Files Are Encrypted
Once Key Manager activates, video (Screen Capture) encryption is enabled automatically.
Web Access Is Encrypted
The Tomcat web server installed and configured for the Quality Management applications utilizes secure-socket layer (SSL) encryption.
Audit Log
Audit Logs Are Collected
Analysis and monitoring of systems allows for breach detection. The following Audit functionality allows for the monitoring of user activity within Eleveo products.
Audit Log - The Audit Log tracks User actions and is useful for monitoring activity.
By default audit logs are collected. Audit logs are saved to the database. They can also be viewed in the Web UI.
The WFM application is not linked to the Audit log at this time.
Searching in the Conversation Explorer
Searching by Tags
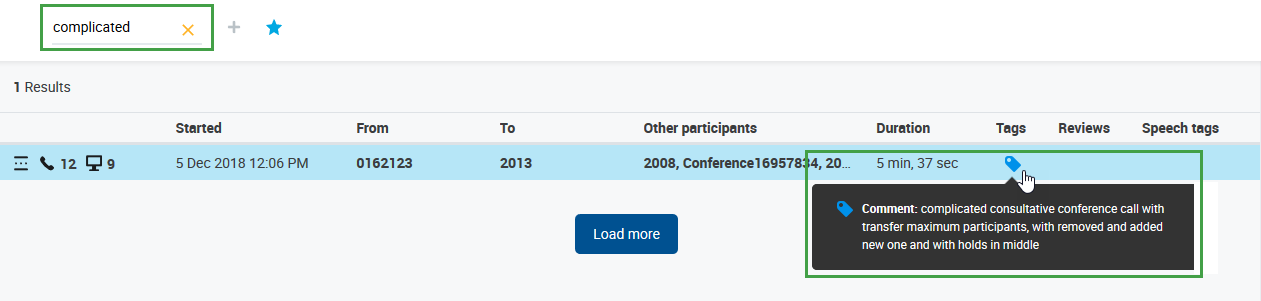
Tags are a great way to mark conversations for future references, such as for quality management or compliance purposes, use the Tags filter to quickly find tagged conversations.
Type in the tag name to quickly find it, useful in the case of many tags. As you start typing, you will see the available options with a match highlighted.
Alternatively, use the scroll bar to see all available tags and to find the tag you need.
Use the corresponding check boxes to choose one or more tags. Already selected tags will also be displayed in the form of an icon next to the filter name. To remove a selected tag, uncheck its checkbox. To remove all checked tags click (x) Reset.
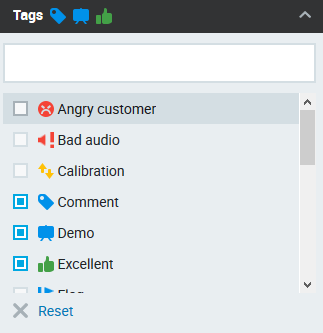
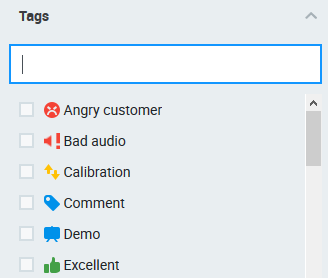
As soon as you make your tag(s) selection conversations will be filtered by the chosen tags.
When multiple tags are selected any conversation with one or more matching tags will be displayed. The search logic used for multiple tags is OR.
You may also use the Full Text Search to find conversations with particular text contained in the tag's comments. The text is case insensitive.
Data Tags
Tags can also have an associated data Key-Value pair and thus two additional behaviors:
If you add such a tag to a conversation, the corresponding Key-Value pair will be applied to the metadata of all conversation's segments. Modifying or deleting such a tag will also affect the metadata Key-Value pair.
When metadata for a segment includes the corresponding Key-Value pair, it will be visualized as this data tag automatically by the system. This visualization is not a user-added tag and cannot contain comments. However, it can be used to modify metadata directly for just one segment by changing the data tag to another data tag or deleting it completely.
In addition to any user-added tags, the application will show a data tag for each segment with the corresponding Key-Value pair. This means that in a conversation you should see 1 tag that was added by a user plus as many tags as the number of segments with the corresponding Key-Value pair. Segments without the corresponding Key-Value pair in the source DB won't show the data tag, resulting in there being fewer tags than segments in the conversation. This could potentially occur when you delete the tag from one of the segments in the QM Conversation Explorer.
Changes to the data tags will also be propagated back to the conversation's metadata (couple_extdata table) stored in the database.
EXAMPLE: When you use a GDPR tag for a conversation with, say, 7 segments, you will see 8 tags in total (1+7). If one metadata representing GDPR tag is removed via the Conversation Explorer, you will see that there are 7 segments, but 1+6 tags.